Hashing vs Salting: How do these functions work?
The practical explanation of using hashing & salting with real-life example
Definitions
Hashing converts plaintext data elements into consistent ciphertext outputs for data verification.
Salting adds random characters to data, like passwords, to stop hackers from looking for consistent words and phrases in sensitive data to decode it.
Real-world usage of hashing
As software developers, we may come up with a scenario or task in which we want to store a username & password in the database. If we store a user password or any other sensitive data directly in a database it's easy for hackers to find all the user passwords once the database password got compromised. So, to store these sensitive data of users in a database. we can use a hash function to convert the password & store it in a database now even hackers can see a password field but cannot get an actual password.
Definition explanation :
Hashing converts plaintext data elements into consistent ciphertext
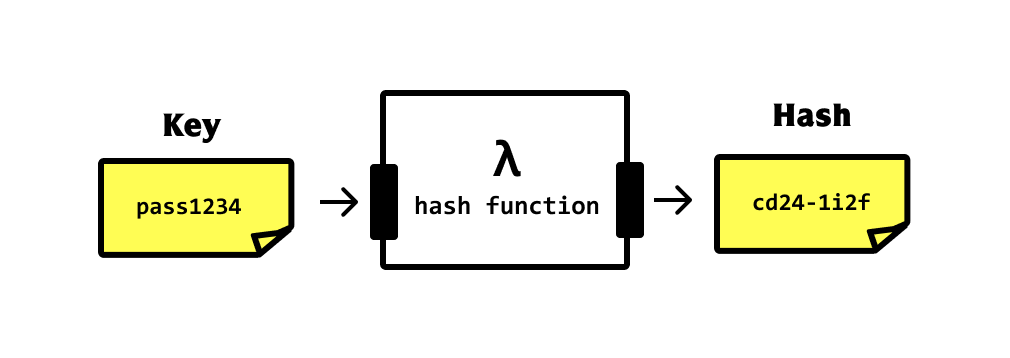
The hashing function converts the plain text into some random set of characters with a defined length. I hope now, the definition makes sense. let's, dive deeper into hashing functions.
Note :
Hashing is a one-way method of hiding sensitive data.
Hashing always returns a fixed length
Hashing a plaintext into a unique ciphertext that cannot be reverted to the original plaintext, without considerable effort.
Hashing Algorithms
There are different hashing algorithms some of the common algorithms are
SHA-1 - [ 160-bit (40-characters) ]
SHA-2 - [ 256-bit (64-characters) ]
MD5 - [ 128-bit (32 -characters) ]
SHA - 1 Hash
SHA-1 hash Is the most commonly used hashing function that converts plain text into a 40-character-long ciphertext. If the password is hashed & saved in a database it seems like a reference below.
| username | password |
| Alice | 4420d1918bbcf7686defdf9560bb5087d20076de5f77b7cb4c3b40bf46ec428b |
| Jason | 695ddccd984217fe8d79858dc485b67d66489145afa78e8b27c1451b27cc7a2b |
| Mario | cd5cb49b8b62fb8dca38ff2503798eae71bfb87b0ce3210cf0acac43a3f2883c |
As we know hashing a string cannot be converted back into plain text without a considerable amount of effort.

What is Salting?
Salting a piece of data is done by adding additional random characters to the text to strengthen it. This is most often done with passwords by adding random characters to the beginning or end of a password to prevent it from being easily guessed by a hacker.
Real-world usage of salting
Hashed passwords are not unique to themselves due to the deterministic nature of the hash function. when given the same input, the same output is always produced. let's consider two users Sai & Saravana uses the same password pwd123
Saravana | 4420d1918bbcf7686defdf9560bb5087d20076de5f77b7cb4c3b40bf46ec428b |
Alice | 695ddccd984217fe8d79858dc485b67d66489145afa78e8b27c1451b27cc7a2b |
Sai | 4420d1918bbcf7686defdf9560bb5087d20076de5f77b7cb4c3b40bf46ec428b |
As we can see, Sai and Saravana has the same password as we can see that both share the same hash4420d1918bbcf7686defdf9560bb5087d20076de5f77b7cb4c3b40b .The hacker can better predict the password that legitimately maps to that hash. once the password is known, the same password can be used to access all the users that use that hash.
To prevent this the technique called salting is used, salt is a random character generated & appended to a plain text which makes that hash unique & impossible to crack.
Example for salting
user password : pass123
salt : crack
salted-text : pass123crack
Hashing the salted text generated a new unique hash & this demonstrates the importance of using salts. Simple techniques, like hashing and salting, may not seem revolutionary. Yet they protect sensitive data without adding much additional challenge to the existing system.
Salted hashes can still be cracked. It just takes more effort and time and the hashes can't be looked up in hash databases.
Conclusion
This article is to explain the simple usage of Hashing & Salting. There are a ton more things to cover. Please share & like Feel free to share your inputs in the comments for improvements
